It feels like every day, we hear about another data breach or ransomware attack against companies large and small. It’s one of the downsides of such rapid technological growth – just as quickly as cybersecurity professionals can increase defences, bad actors are expanding their attack arsenals.
To decrease the risks, individuals and businesses alike must do what they can to protect their personal and customers’ information. Multi-factor authentication (MFA) is one step that everyone should be taking to add an extra layer of security to account logins.
MFA requires additional confirmation of a user’s identity other than simply inputting a password. This may seem like a quick fix, but there can be some complexity to the setup process when implementing it across a whole company. We’ll explain the importance of employing multi-factor authentication and offer some steps businesses can take to set up MFA to protect their systems.
The risks
A cybersecurity breach is always costly for businesses. Breaches are expensive simply because of ransoms or other financial burdens; they come with other significant risks such as lost customer trust.
In 2020, there were thousands of confirmed data breaches affecting everyone, from small companies to tech giants like Microsoft. Incidents like ransomware and malware attacks, phishing scams, and other hacks expose personal data daily. These attack vectors are made even more expansive with the rise in cloud computing, the Internet of Things (IoT), digital banking, and many other advancements that make our digital lives more convenient and more dangerous.
One of the biggest problems is that humans will still be vulnerable no matter how advanced tech gets; one thing, people are notoriously bad at password generation. Most people use passwords that they can remember, which means they can also be guessed or brute-forced using databases of common passwords. Most people also use the same password for more than one account, so one tiny breach and all your funds can be at risk.
There has already been some push to address this risk. Multi-factor authentication (MFA) is widely adopted, usually taking the form of an email or text-based code sent to a user’s phone or email. Unfortunately, standard MFA solutions are not all that secure.
Phones can be stolen, and many don’t have protection beyond a four-digit screen lock PIN (which can be brute-forced). Similarly, email accounts can be easily compromised, and people are susceptible to email phishing schemes. This means we need another layer over simple passwords and MFA.
How MFA can help
Adding extra layers of security can make it much harder for hackers to access your online accounts, and MFA is one of the least time-consuming or intrusive ways to do this. It’s so crucial that companies like Google require MFA for all users to decrease the risk.
You should implement MFA even if you think your system is secure. According to cybersecurity expert Ludovic Rembert of Privacy Canada, you should always have multiple layers of protection, even for something like a private WiFi network or a home security system:
“If any of your devices are connected via wifi, then [hackers] can also gain access to your network in general,” Rembert says. “To ensure that this doesn’t happen, you can make extremely long passwords with unique symbols, change your password frequently, check security settings, or use an extra layer of protection with encryption software.”
The increasing ubiquity of IoT devices and cloud-based solutions makes this even more critical. During the pandemic, work from home rendered it more necessary for companies to provide remote devices and secure connectivity for their employees. Unfortunately, cloud-based solutions and IoT devices add complexity to cybersecurity infrastructures, and there have been numerous cases proving the vulnerabilities of such devices.
MFA adds layers of security by requiring that you prove your identity in more than one way. Authentication is typically established through three options: something you know (e.g. password or PIN), something you have (e.g. a smart card or security token), and something you are (e.g. fingerprint or voice recognition). MFA works by combining at least two of these options for added security.
What’s more, MFA options are becoming even more advanced by harnessing artificial intelligence (AI) for behaviour-based authentication. So-called intelligent authentication provides more personalised verification by taking into account the location, IP address, timing, etc., of logins in addition to traditional credentials. This offers a peek at the future of MFA, which could add even greater security for organisations in combination with digital identity management protocols.
How to set up MFA
While MFA is one of the less burdensome security measures from the user’s perspective, choosing the right solutions can still be challenging for businesses. Here are a few tips to keep in mind when employing multi-factor authentication for your organisation.
Diversify your authentication steps
There are many choices of which factors to incorporate into your MFA. We’ve already mentioned one-time passwords (OTPs), and while those alone may not be enough, they can be an easy way to make hackers’ jobs harder without making your employees’ jobs more frustrating. Security questions are similar; they’re not enough on their own, but it is multi-factor, after all.
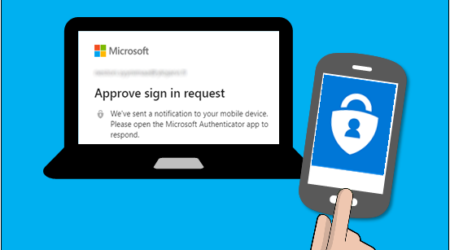
Software token authentication, or push-based authentication, is a similar but stronger alternative to SMS-based OTPs. This requires an additional application to verify logins, but .it shouldn’t be a hassle for users once it’s set up. A push is more secure because it’s out-of-band, meaning it takes place over a secure connection physically separate from the primary network.
These notifications are sent over an encrypted channel, and they don’t contain an actual code. While SMS-based OTPs could be read from a locked phone screen, pushes must be confirmed by unlocking the device and clicking the confirmation. Your MFA software should use digital certificates and encryption for at least one layer, no matter what solutions you choose.
MFA need not be a pain for IT (or users)
Setting up MFA doesn’t have to be a nightmare for your IT department. Many businesses – especially SMEs – avoid it because they think it will be a hassle. Still, you can focus on flexible solutions to widely deploy solutions that will integrate with your existing infrastructure and be installed without having to visit every device for manual setup.
As with anything, user experience is something to look for in such software – both an unburden some experience for employees and a streamlined setup for administrators. And even if you don’t have the infrastructure for intelligent authentication yet, you can incorporate your behavioural settings, such as taking timing and simultaneous device connections into account, so users don’t have to authenticate before every single use.
Educate your employees about security
It’s unfortunate but true: humans are usually the weak link. As you implement MFA, you should simultaneously educate your employees about choosing appropriately long and complex passwords, as well as recognising the signs of phishing scams and other questionable activity.
You can teach them how to use MFA on personal devices as well. Especially if they’re working from home, they probably read work emails and such on their mobile phones. Ensure your employees use VPNs for laptops and phones and only store proprietary data on company-secured devices and servers.
If you have the infrastructure to accommodate it, biometric data is probably the most hard-to-hack MFA solution. But even if you can’t implement it. Company-wide, keep in mind that most smartphones have this capability already. Encourage employees to use fingerprint locks for their work phones as well as their devices.
Conclusion
When done correctly, MFA is one of the simplest and least burdensome forms of security that a company can implement. Considering the rampant cybersecurity risks in today’s digital landscape, there are no reason businesses and individuals shouldn’t be taking advantage of this solution. If you invest in the most up-to-date tools, your multi-layered security infrastructure will go far in protecting your employees and sensitive data.